Kaspersky shares reminders for enterprises, employees to keep their data safe amidst work-from-home
6 December 2021
A report published last August shown that 69% of Malaysia workforces have indicated their preference to continue working from home, highest in the region, ahead of Singapore, China and Hong Kong.
Having more employees working from home opened up new vulnerabilities that cybercriminals were quick to target. The volume of corporate traffic grew as well as more users moved to using third party services to exchange data and work through potentially insecure Wi-Fi networks.
One of the most popular application-level protocols for accessing Windows workstations or servers is Microsoft’s proprietary protocol – remote desktop protocols (RDP).
RDP empowers Malaysians to continue working remotely. However, this working method has a potential for cyber attempts one of which is a brute force attack that targets the protocols employees use to remotely access company resources. A brute force is an attempt to test all different usernames and passwords until the correct combination is found, and they gain access to company resources.
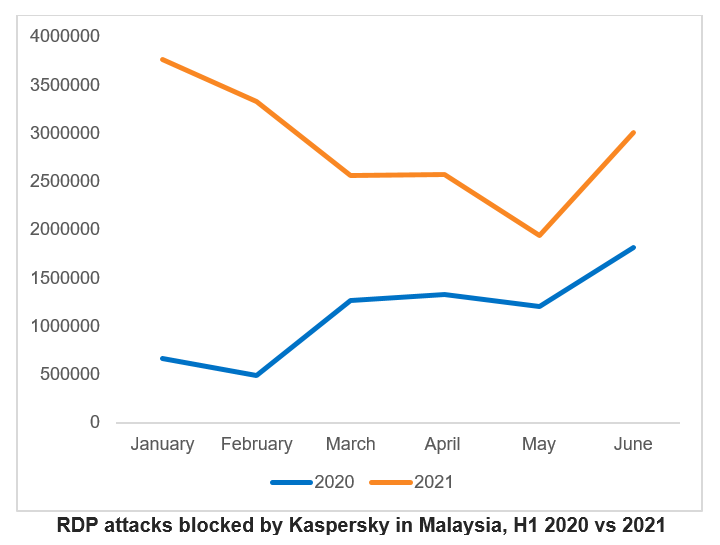
In Malaysia, the total RDP attacks detected in the first six months of 2021 grew by 53.6% compared to the same period last year. Between January to June 2021, Kaspersky recorded a total of 10.4 million attacks attempts against Kaspersky users in the country with Microsoft RDP installed on their desktops. This is a significant spike compared to 6.78 million in the first half of 2020.
Globally, Kaspersky has detected 377.5 million brute force attacks against RDP.
“Under normal circumstances, moving an entire workforce from a secure IT enterprise environment to a home network with adequate cybersecurity measures requires long-term planning and preparation. The pandemic rob us of this opportunity and our latest RDP attack statistics show that cybercriminals are exploiting this loophole,” comments Chris Connell, Managing Director for Asia Pacific at Kaspersky.
Kaspersky researchers also discovered attacks on other remote access protocols, other than RDP, such as virtual network computing (VNC), which also used for remote access. Companies are advised to closely monitor programs in use and update them on all corporate devices in a timely manner.
RDP attacks blocked by Kaspersky in Malaysia, H1 2020 vs 2021
“This health crisis has clearly expedited digital transformation and the merging of our professional and personal life. Employees are now actively leading the way in accepting changes in pursuit of greater freedom and flexibility, using technology to own a new future. Companies must now adapt and restructure the modern workplace to make it more productive, sustainable, and most importantly, secure,” adds Connell.
To avoid potential cyber threats in the trend of remote work systems, Kaspersky provides recommendations for companies to:
- Provide training on basic cyber hygiene to your employees. Help them to identify the most common types of attacks that occur in the company, and provide basic knowledge in identifying suspicious emails, websites, text messages.
- Use strong, complex and different passwords to access every company resource
- Use Multi-Factor Authentication or two-factor authentication especially when accessing financial information or logging into corporate networks.
- Where possible, use encryption on devices used for work purposes.
- Enable access to RDP through a corporate VPN
- Always prepare for backup copies of critical data.
- Use a reliable enterprise security solution with network threat protection such as Kaspersky Endpoint Security for Business
For employees who are still working remotely, some of the following simple steps can be done in order to stay safe:
- Avoid clicking on suspicious links that come through your email inbox or messaging apps. Even if it comes from your colleagues, if the message contains suspicious content, make sure to check with your colleagues first
- Always check all devices in the house, make sure they have been through updates and are using the latest operating system
- Install security solutions on all devices, as well as solutions for tracking equipment in case of loss.
- Make sure to only download apps only from trusted sources
- Use only good quality and safe internet connection. Avoid using work equipment for personal purposes or vice versa.