20 June 2022
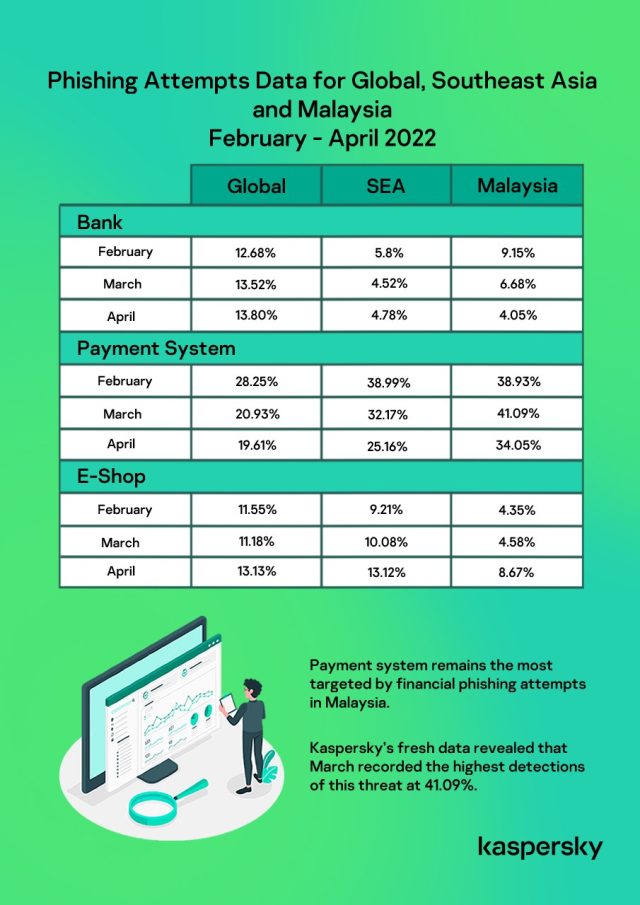
Payment system remains most targeted by financial phishing attempts in Malaysia. Kaspersky’s fresh data revealed that March recorded the highest detections of this threat at 41.09%.
February witnessed the cybercriminals eyeing to victimise users through banking, payment system and online shopping, at 52.43%, just 1.57% lower than overall Southeast Asia region in terms of finance-related phishing attempts.
| Global | SEA | Malaysia | |
| Bank | |||
| Feb | 12.68% | 5.8% | 9.15% |
| Mar | 13.52% | 4.52% | 6.68% |
| Apr | 13.80% | 4.78% | 4.05% |
| Payment System | |||
| Feb | 28.25% | 38.99% | 38.93% |
| Mar | 20.93% | 32.17% | 41.09% |
| Apr | 19.61% | 25.16% | 34.05% |
| E-Shop | |||
| Feb | 11.55% | 9.21% | 4.35% |
| Mar | 11.18% | 10.08% | 4.58% |
| Apr | 13.13% | 13.12% | 8.67% |
Kaspersky’s phishing attempts data for Global, Southeast Asia and Malaysia for the period February – April 2022
The percentages are from anonymised data based on the triggering of the deterministic component in the Kaspersky’s Anti-Phishing system on user computers. The component detects all pages with phishing content that the user has tried to open by following a link in an e-mail message or on the web, as long as links to these pages are present in the Kaspersky database.
Banking and payment system phishing attempts may have been lower since the April 1, 2022. This was the announced start of Malaysia’s border reopening to international travellers, as well as for Malaysians to travel abroad without the need to quarantine.
However the online shopping phishing attempts went up in April to 8.67%, with the possibilities of many looking into online deals that may have promised lucky draws.
“Alongside the increased adoption in digital transactions here in Southeast Asia, we also see the rise of “Super Apps” in the region. These are the mobile applications that combine all popular monetary functions including e-banking, mobile wallets, online shopping, insurance, travel bookings, and even investments. Putting our data and digital money in one basket can trigger an aftermath snowball, with the impact of a phishing attack swelling at an unforeseeable rate,” says Yeo Siang Tiong, General Manager for Southeast Asia at Kaspersky.
Super Apps are traditional banks and service providers’ way of standing out in a rather crowded industry. As they try to work with third parties and incorporate their services into a single mobile app, the attack surface expands, opening up more doors of a malicious exploit.
Phishing has remained to be the most effective trick on cybercriminals’ sleeves. It is a known way to crack into a user’s or even a company’s network by playing on a user’s emotions.
A possible scenario is given that one app has all the financial details of a user, a simple phishing link asking for the user’s credentials can compromise all the data available in the app. This magnifies the possible damaging effects of this threat.
“It is known that cybercriminals follow the money trail, so it is important for banks, app developers, and service providers to integrate cybersecurity from the beginning of application development. We expect hackers to target the rising “Super Apps”, both its infrastructure and its users through social engineering attacks. We urge all fintech companies to deploy a secure-by-design approach in their systems and to continuously provide proactive education for their users in this period where phishing attacks continue to thrive,” adds Yeo.
While security systems are in place in most financial companies to protect customers from falling victim to suspicious activity, it is a truth that prevention is better than cure; much more can be proactively done at both the individual and bank level.
For enterprises, the most important method of protection is to keep in mind that cybersecurity should be a “living” strategy, not a static platform. This will blend technology and effort, and is constantly upgraded, updated and improved.Banks and service providers need to ensure a security team (or security experts) who will be able to ensure cyber defence infrastructure is updated, and will be able to provide support in the event of a cyberattack.
To start, firms can invest in endpoint security solutions. Kaspersky currently offer its Endpoint Detection and Response Optimum at 35% off to help enterprises get started with. Interested companies can visit this link to know more.
Some more crucial steps to consider also include:
- Consider a threat intelligence platform: Another key component to include would be to ensure access to the latest IT security trends/threats – that is also known as threat intelligence. Threat intelligence will give the insight to act on, and paint a bigger, more accurate picture of the bank’s digital presence, to educate senior stakeholders about the ongoing risks and vulnerabilities. This will empower them to be able to make informed decisions on what needs to be done to keep the potential harm at bay, refine existing security processes to better defend against known threats and to plug any gap the IT infrastructure on an ongoing basis.
- Ensure any third party vendors’ cybersecurity systems are also updated. There have been increasing reports on how breaches to third-party security systems have implicated businesses. Whether you are the bank, the Government or a private enterprise, no one is immune from these security threats, and it is important that we heighten our vigilance when it comes to cybersecurity. It does not matter how secure your third-party vendor tells you their systems are, as the elevated prominence of supply chain attacks have shown us that it is important to take responsibility for your own cybersecurity posture rather than leaving it in your partners’ hands.
- Being the parties impersonated by threat actors, the implementation of defence measures need to go beyond protecting their systems. Banks need to take proactive measures to remind their customers against falling prey to their impersonators and their phishing and scam attacks, even if they happen outside of their systems.
Some things to keep in mind that can help individuals protect themselves against phishing attacks include:
- Do not respond: even prompts to reply like texting “UNSUBSCRIBE” or “STOP” can be a trick to identify active phone numbers. Attackers depend on your curiosity or anxiety over the situation at hand, but you can choose not to engage.
- Avoid using any links or contact information in the email or message: go directly to contact channels where possible. Furthermore, urgent notices can be verified directly on online accounts or via an official phone helpline.
- Look out for mistakes, typos and strange characters in the text: some threat actors really struggle with English, or some mistakes are intentionally made (such as using numbers to replace certain alphabets, eg “Bank L0an” instead of “Bank Loan”) in an attempt to bypass spam filters.
- Slow down if a message is urgent: the nature of emails and SMS are that they are often read on the go, when one is distracted or in a hurry and thus leaving one’s guard down. Approach offers as caution signs of possible phishing, remain calm and proceed carefully.
- Download an anti-malware app, which can protect against malicious apps such as Kaspersky Total Security for a safety net.
Read Kaspersky’s full 2021 Threat Landscape Report for Southeast Asia here https://kasperskysea.co/premium_report.